ThreatConnect Python Snippets
Sublime Text snippets for writing scripts in less than 60 seconds that use ThreatConnect's Python SDK.
Details
Installs
- Total 2K
- Win 1K
- Mac 204
- Linux 422
| Feb 20 | Feb 19 | Feb 18 | Feb 17 | Feb 16 | Feb 15 | Feb 14 | Feb 13 | Feb 12 | Feb 11 | Feb 10 | Feb 9 | Feb 8 | Feb 7 | Feb 6 | Feb 5 | Feb 4 | Feb 3 | Feb 2 | Feb 1 | Jan 31 | Jan 30 | Jan 29 | Jan 28 | Jan 27 | Jan 26 | Jan 25 | Jan 24 | Jan 23 | Jan 22 | Jan 21 | Jan 20 | Jan 19 | Jan 18 | Jan 17 | Jan 16 | Jan 15 | Jan 14 | Jan 13 | Jan 12 | Jan 11 | Jan 10 | Jan 9 | Jan 8 | Jan 7 | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Windows | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 |
| Mac | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Linux | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Readme
- Source
- raw.githubusercontent.com
ThreatConnect Python SDK Sublime Text Snippets
The goal of this project is to make snippets such that you can write a useful python script that talks with ThreatConnect's API in less than less than 60 seconds.
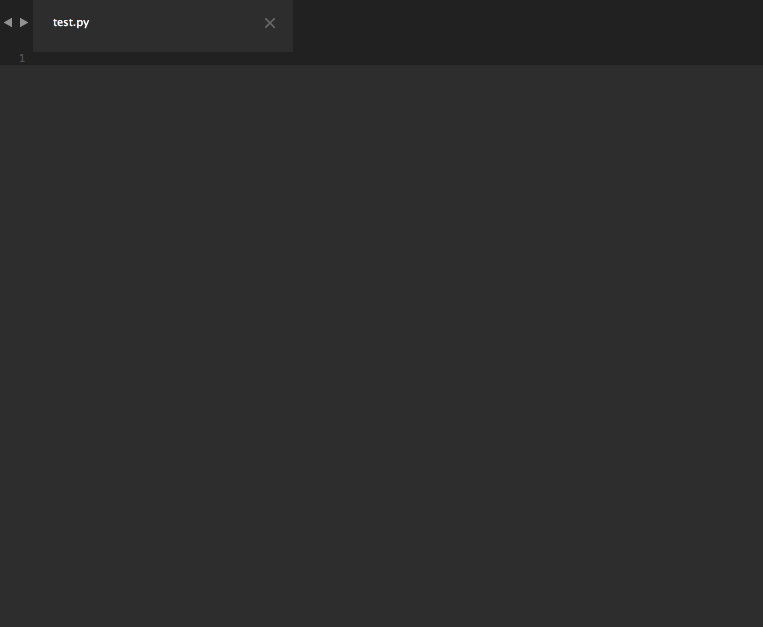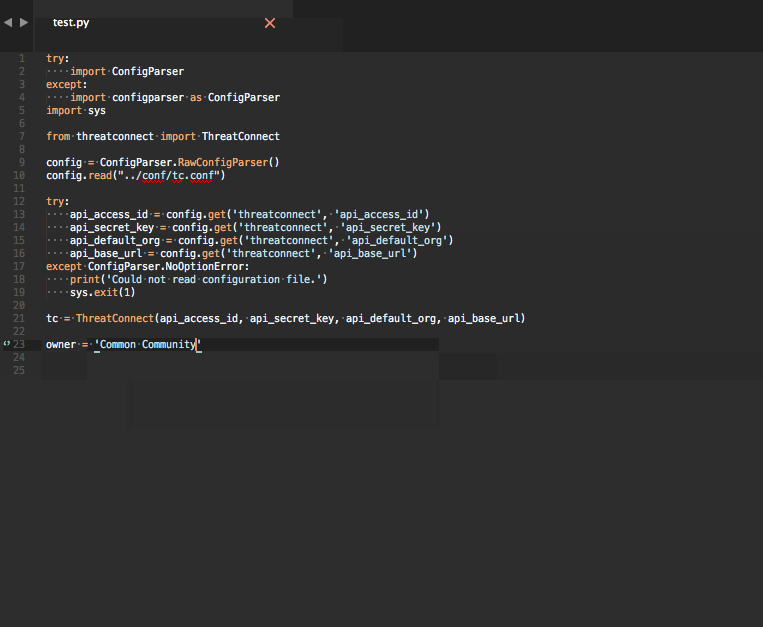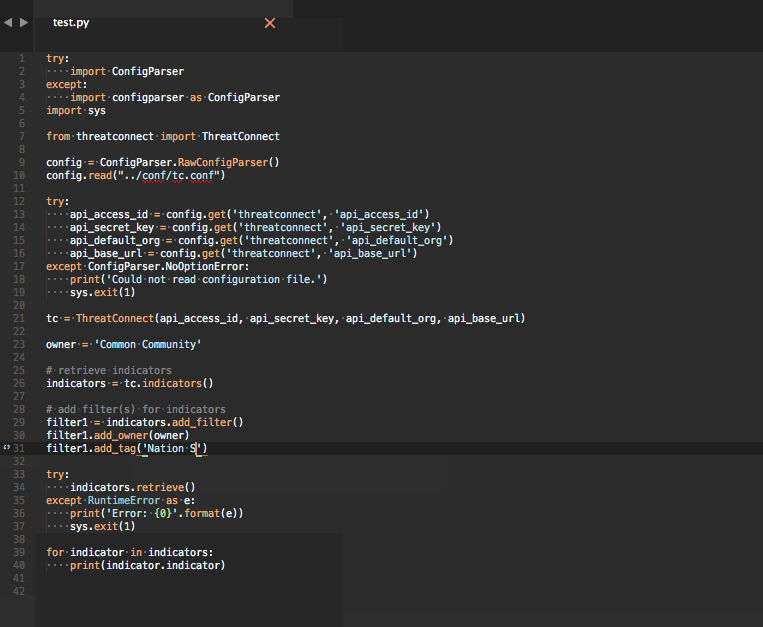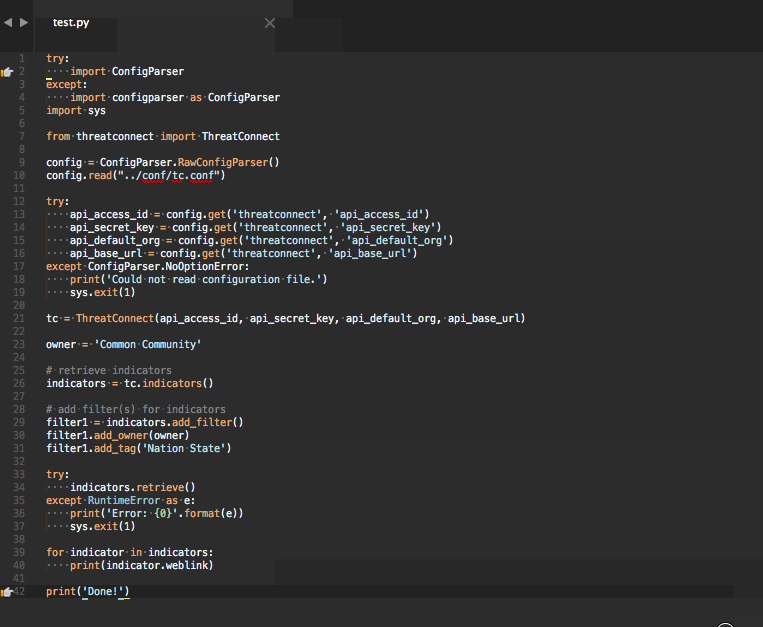
As the name implies, you will need access to ThreatConnect's API before these snippets are useful. Additionally, these snippets are designed for use with Sublime Text. If you haven't tried it yet, I strongly encourage you to do so.
Snippet Design Paradigm
If a paradigms isn't worth your time, feel free to jump to the Examples section below (I don't want to shortchange anyone). For the rest, each snippet is constructed as follows:
tc<action><object>
The <action> is usually one letter that represents what we want to do (refer to the Actions section below). The <object> specifies the type of object (refer to the Objects section below for a list of possible objects) to which the aforementioned action will be done. For you language buffs, the <object> is really an indirect object.
Actions
| Desired Action | Action Prefix | Description |
|---|---|---|
| Retrieve | r |
Retrieve something from ThreatConnect |
| Create | c |
Create something in ThreatConnect |
| Update | u |
Update something that already exits in ThreatConnect |
| Delete | d |
Delete something from ThreatConnect |
| Add/set Metadata | a |
Add metadata to an object |
| Load Metadata | l |
Load metadata about an object |
| Filter | f |
Filter objects when retrieving |
Objects
List of possible objects coming soon…
Examples
tcrindicators: In this snippet,ris the action (it stands for “retrieve”) andindicatorsare the object. Thus, this snippet provides code to retrieve indicators.tcrgroups: In this snippet,ris the action (it stands for “retrieve”) andgroupsare the object. Thus, this snippet provides code to retrieve groups.tccindicator: In this snippet,cis the action (it stands for “create”) andindicatoris the object. Thus, this snippet provides code to create an indicator.tclattributes: In this snippet,lis the action (it stands for “load”) andattributesare the object. Thus, this snippet provides code to load the attributes for an object.
Complete List of Snippets
Helpful Utility Snippets
tccommit: Generic committcconfig: TC configuration headingtccustomcall: Make a custom API calltcdelete: Generic deletetcfilter: Add a filtertcfilterparam: Add a filter parametertcpostfilter: Add a post filtertcretrieve: Generic retrievetctime: Time format for TC's Py SDK (REQUIRES: from datetime import datetime)
Groups
Retrieving Groups
tcradversaries: Retrieve adversariestcrcampaigns: Retrieve campaignstcrdocuments: Retrieve documentstcremails: Retrieve emailstcrgroups: Retrieve groups (all group types)tcrincidents: Retrieve incidentstcrsignatures: Retrieve signaturestcrthreats: Retrieve threats
Creating Groups
tccadversary: Create adversarytcccampaign: Create campaigntccdocument: Create documenttccemail: Create emailtccincident: Create incidenttccsignature: Create signaturetccthreat: Create threat
Updating Groups
tcuadversary: Update adversarytcucampaign: Update campaigntcudocument: Update documenttcuemail: Update emailtcuincident: Update incidenttcusignature: Update signaturetcuthreat: Update threat
Deleting Groups
tcdadversaries: Delete adversariestcdcampaigns: Delete campaignstcddocuments: Delete documentstcdemails: Delete emailstcdincidents: Delete incidentstcdsignatures: Delete signaturestcdthreats: Delete threats
Indicators
Retrieving Indicators
tcrindicators: Retrieve indicators (all indicator types)
Multi-Retrieve
tcrmaddresses: Retrieve multiple IP addressestcrmemailAddresses: Retrieve multiple email addressestcrmfiles: Retrieve multiple file indicatorstcrmhosts: Retrieve multiple hoststcrmurls: Retrieve multiple URLs
Single Retrieve
tcrsindicator: Retrieve a single indicator
Creating Indicators
tccindicator: Create indicatortccfileindicator: Create a file indicator
Deleting Indicators
Coming soon…
Tasks
Retrieving Tasks
tcrtasks: Retrieve tasks
Creating Tasks
tcctasks: Create a task
Updating Tasks
tcutasks: Update a task
Victims
Coming soon…
Metadata
Loading/Retrieving Metadata
tclassocgroups: Retrieve associated groupstclassocindicators: Retrieve associated indicatorstclassocvictims: Retrieve associated victimstclassociations: Load associationstclattributes: Load attributestclfileoccurrences: Load file occurrencestclsecurity_labels: Load security labelstcltags: Load tags
Adding Metadata
tcaassocgroup: Add an associated grouptcaassocindicator: Add an associated indicatortcaassocvictim: Add an associated victimtcaattribute: Add an attributetcaratings: Add threat and confidence ratingstcasecuritylabel: Add a security labeltcatag: Add a tag
Updating Metadata
Coming soon…
Deleting Metadata
Coming soon…
Installation
If you're using Package Control for Sublime Text, simply install the ThreatConnect Python Snippets package.
Alternatively, you can clone this repository directly into your Sublime plugin folder and install the snippets manually as described below:
OSX
cd ~/Library/Application Support/Sublime Text 3/Packages
git clone --depth 1 https://github.com/fhightower/threatconnect-python-snippets.git
Linux (may vary based on distro.)
cd ~/.config/sublime-text-3/Packages
git clone --depth 1 https://github.com/fhightower/threatconnect-python-snippets.git
Windows
cd "%APPDATA%\Sublime Text 3\Packages"
git clone --depth 1 https://github.com/fhightower/threatconnect-python-snippets.git
Note: If you are having trouble finding the correct location to install the snippets, refer to the documentation on the subject.
Credits
The framework for this package was created from the Sublime Text Snippet Template available here: https://github.com/agenoria/sublime-snippet-package-template.
The documentation was automatically generated using the script here: https://github.com/fhightower/sublime_snippet_documenter.
